[ad_1]
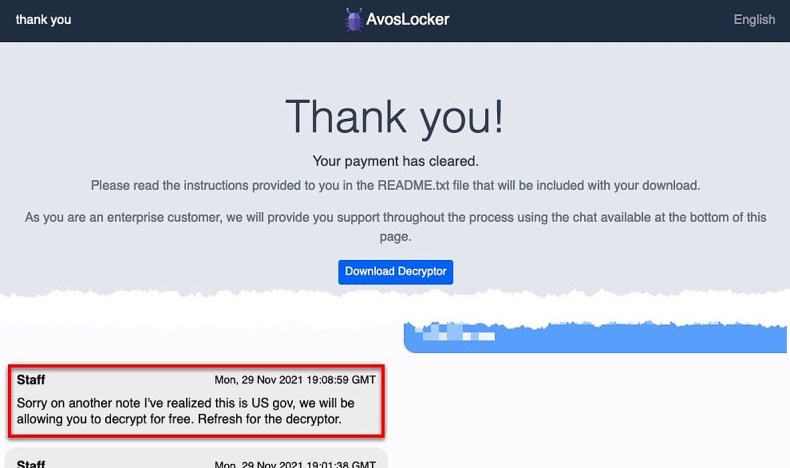
The AvosLocker ransomware operation provided a free decryptor after learning they encrypted a US government agency.
Last month, a US police department was breached by AvosLocker, who encrypted devices and stole data during the attack.
However, according to a screenshot shared by security researcher pancak3, after learning that the victim was a government agency, they provided a decryptor for free.
Source: Twitter
While they provided a decryptor to the police department, the ransomware operation refused to provide a list of stolen files or how they breached the department’s network.
A member of the AvosLocker operation told BleepingComputer today that they have no policy on who they target but usually avoid encrypting government entities and hospitals.
“You should note, however, that sometimes an affiliate will lock a network without having us review it first,” the AvosLocker operator told BleepingComputer.
When asked if they purposely avoid targeting government agencies out of fear of law enforcement, they said it’s more because “tax payer money’s generally hard to get.”
However, international law enforcement operations have resulted in numerous indictments or arrests of ransomware members and money launderers over the past year. These arrests include members of the REvil, Egregor, Netwalker, and Clop ransomware gangs.
This increased pressure is shown to have a good effect, leading to numerous ransomware operations shutting down, including the DarkSide, BlackMatter, Avaddon, and REvil operations.
Unfortunately, many of these ransomware gangs just rebrand as a new operation, thinking it will help them evade law enforcement.
Even with these arrests and increased pressure, AvosLocker said they are not worried about law enforcement as they “have no jurisdiction” in the “motherland.”
[ad_2]
Source link
