[ad_1]
Trezor recently published a warning against a new phishing campaign targeting its users. The phishing campaign seems to have been effective for several reasons we are going to detail.
Clever targeting
Many companies provide mailing lists to their customers. More often than not, those lists aren’t directly handled by the company, but via third parties. Trezor, for example, uses MailChimp to spread information to its customers.
Now if someone gets illegitimate access to the database used for such mailing activity, they might target companies’ customers without targeting non-customers, and strengthen their social engineering schemes to lure victims in.
It seems that this is exactly what happened. According to Trezor, MailChimp confirmed that its service has been compromised by an insider targeting crypto companies (Figure A).
Figure A
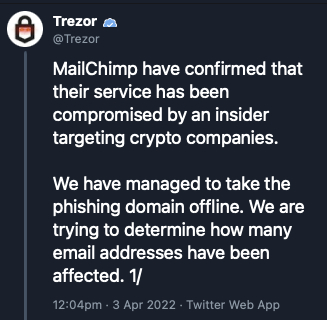
Once in possession of a list of email addresses belonging only to real Trezor customers, the attackers moved to the next step.
The phishing email
A convincing email was sent to Trezor’s customers who were part of the mailing list database stolen from MailChimp (Figure B).
Figure B
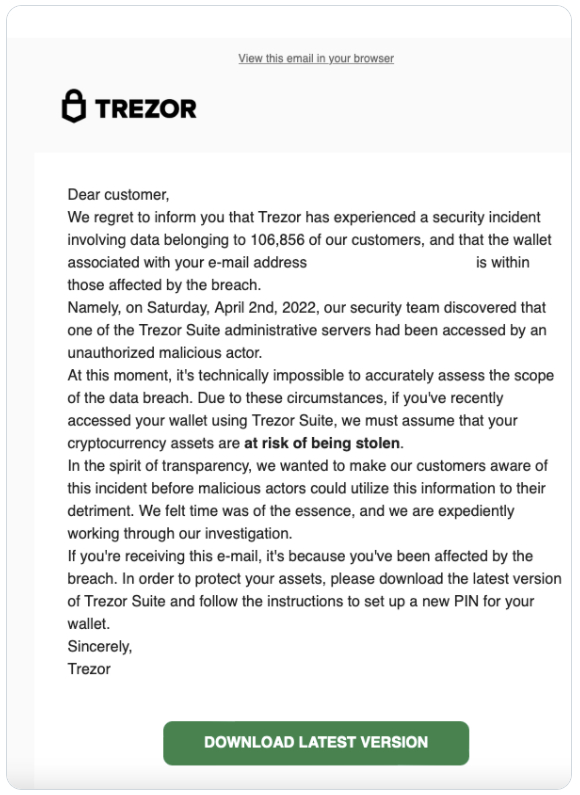
As you can see, the email states that Trezor suffered from a severe security incident that might lead to cryptocurrency asset theft. It says that the affected users who receive the email should download the latest version of Trezor Suite and follow the instructions to protect their assets and set up a new PIN for their wallet.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
The phishing website
Users clicking on the link contained in the phishing emails are led to a phishing website hosted at suite.trẹzor.com. A trained eye might see a little dot under the “e” character from trezor : “ẹ”. This technique of using special Unicode characters has been a tactic for years and is known as a Unicode domain phishing attack. And a careful user might also have noticed that the real website for Trezor Suite is actually suite.trezor.io, not .com. These are two good reasons not to click and not to move further in that fraud, but unfortunately the signs are east to overlook.
The fake website is visually an exact copy of the legitimate one (Figure C).
Figure C
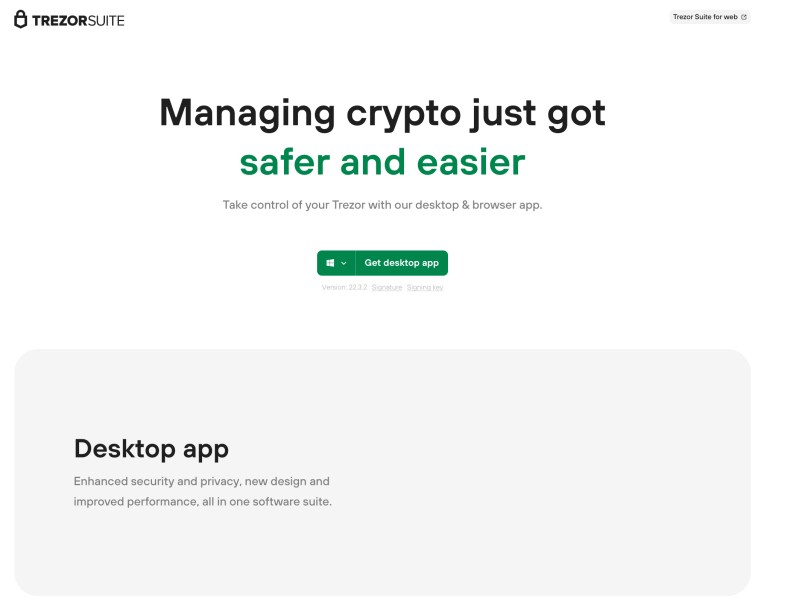
The fake application
The fake website offers the application for the Windows, Linux and Macintosh operating systems.
TechRepublic downloaded and tested the Windows version of the software. After it’s launched, the program quietly asks the user to install Trezor Suite. Once executed and installed, the software opens and reveals content similar to the legitimate site. It even shows a banner warning the user against recent phishing attacks, reinforcing the assurance that everything is being done to protect users and that everything is safe (Figure D).
Figure D
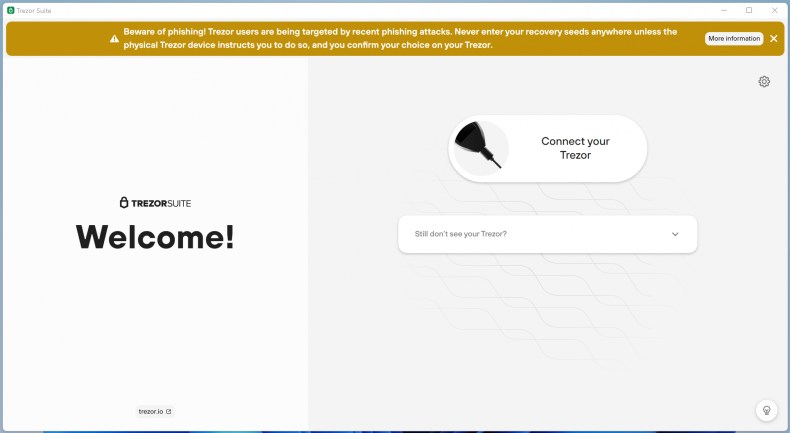
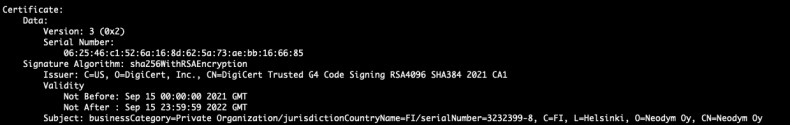
Only careful examination of the downloaded software could hint at its being fake. The software has been signed with a certificate from a Finnish company, “Neodym Oy,” which might have been compromised (Figure E). Legitimate files originating from the Trezor website would have been signed by “SatoshiLabs, s.r.o.”
Figure E
While it sounds like a huge effort to produce such a fraudulent application, it is actually a straightforward task for any developer, as the source code for the application is free and available online.
SEE: Security incident response policy (TechRepublic Premium)
The final stage: The theft
After the user connects the Trezor device to the fake application, they are prompted to enter the recovery phrase for the wallet, which is sent to the cybercriminals. Once in possession of the recovery phrase, it is easy to use it to steal the cryptocurrency assets.
How to protect from this kind of threat
Users should always update their software from the legitimate provider website. They should never use any link provided in an email. Responsible providers will not send email links to their users when it comes to software updates.
The provider’s URL should always be carefully checked. In the case reported here, the cybercriminals used suite.trẹzor.com instead of suite.trezor.io.
It’s also a good idea to bookmark the legitimate URL in the browser, and then rely only on this bookmark, never on emails.
As for the cryptocurrency hardware wallets from Trezor, the recovery phrase should never be typed in any software or website. It should only be typed on the device.
Should any doubt remain, users should reach the provider for more information.
In addition, it is advised to use a dedicated email address for every different mailing list. This way, the source of a data leak can be immediately known and can provide a good warning to a user who suddenly gets unrelated content to an email address they used for only one purpose.
Finally, users should always keep their operating systems and software up to date, since there are other ways to steal cryptocurrency assets from computers, and more and more malware is getting wallet-stealing functionalities.
These cybersecurity best practices should be included in your Security Awareness and Training sessions.
Update
The orange banner on the fake application has changed and now shows a red banner saying that the running software is fake, and that the user should exit the program immediately (Figure F).
Figure F
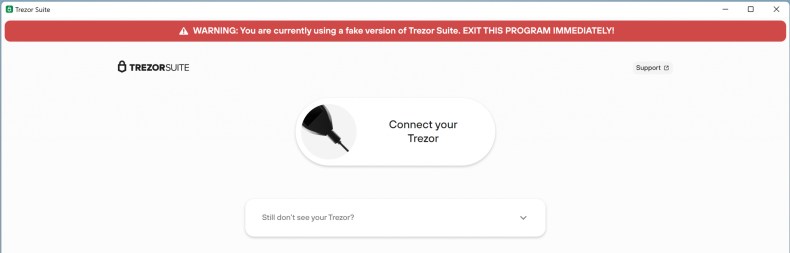
As can be seen, the cybercriminals did not modify the actual code that fetches the banner content from Trezor. It seems that Trezor took this opportunity to change the banner content so that the fraudulent application actually warns the users running it.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
[ad_2]
Source link
